If you use SMS passcodes when signing in to university resources with Duo, you will need to select a different option before October 30.
SMS passcodes are the least secure option when using Multi-Factor Authentication and the university is removing the SMS option beginning October 30 to help better protect university resources from cyber criminals. MFA also helps protect personal information, such as access to direct deposit.
 What you need to do:
What you need to do:
Determine whether you will use the Duo mobile app on a tablet or smartphone or use a token (key) that you plug in to your PC or laptop.
If you select the Duo Mobile app option, download and install it on your smartphone or tablet.


If you select the token, you can obtain one from the WebStore.
Faculty and staff who do want to use a token should contact their department for instructions on acquiring a token from the Webstore.
Choosing a Device
- Duo Mobile App - With the Duo Mobile app, you will simply receive a push notification to approve authentication requests, instead of typing in a code.
- You can use a tablet in lieu of a smartphone.
- One advantage of using the Duo Mobile app is that you can receive push notifications over Wi-Fi. This is helpful when you're in an area where you cannot get a cellular signal, or when traveling abroad.
- You can also use the Duo Mobile app even if you are offline and have no access to data, via the Duo Mobile passcode option.
- Hardware Token / Security Key - These can be a good option if you do not want to use your smartphone for authentication. Information on hardware tokens can be found at this help article: Multi-Factor Authentication (MFA), Hardware Tokens and Security Keys.
Once you have made your choice and either have the token in hand or have the app installed you can change your second factor as registered in the NetID Center to your new option following the enrollment steps below.
Enrollment
There are two ways to enroll in multi-factor authentication:
Instructions
- Navigate to the NetID Center (https://identity.uillinois.edu) and log in.
- If your account is already enrolled in MFA, you will need to authenticate with one of your existing devices. If you run into issues or do not have your device, please see this help article for more information: Multi-Factor Authentication (MFA), Troubleshooting.
- Once you're logged in, make sure that the email address listed under Recovery Settings is still correct. This email address can be used to get bypass codes in case you cannot authenticate using your devices in the future.
- Click on 'Set up 2FA'.
- If you are not on campus and connected via the campus network: You will be shown a screen with the heading “(!) Must be connected to the University network to register” – you will still be able to enroll, but you will need to confirm your identity by way of one of your recovery options:
- Click the blue “Get registration code” button below the ‘Option 2’ heading.
- Select one of the presented pieces of contact information, which should match the password recovery options confirmed in step 2.
- You will receive a 6-digit “UI Verify Registration Code” there. Enter the numbers at the “Enter registration code” box on the next screen.
- You will be taken to the “Device Setup: Add a Device” screen. Select the type of device you are intending to use for authentication:
- Smartphone (recommended) should be selected for any device with a phone number
- Tablet should be selected for devices that do not have a phone number but can install the Duo Mobile app.
- Hardware token should be selected for MFA token devices purchased from the University WebStore; more detailed instructions here: Multi-Factor Authentication (MFA), Hardware Tokens and Security Keys. [Must be registered through the Duo Universal Prompt]
- Device dependent instructions below.
If enrolling a phone, enter your phone number and click Yes you want to use the Duo Mobile App, then Continue.
If you do not want to provide your phone number when configuring your smartphone, you can hit the back button and set it up as a tablet. With this option you will only be able to receive push notifications or generate passcodes via the Duo Mobile App.

4. Type of Device Platform (if applicable)
Select your device platform, then click Continue.

5. Installing and Activating Duo Mobile
Duo Mobile is an app that runs on your smartphone or tablet and helps you authenticate quickly and easily. You can still authenticate via text message without it, but for the best experience we recommend Duo Mobile.
- Search for Duo Mobile in your app store.
- Download the app.
- Select "OK" when asked if Duo Mobile can send push notifications.
- Select Add Account
- Once the app is installed, click I have Duo Mobile installed.

6. Activate Duo Mobile
Choose the type of tablet you are adding.
Tablets will be iOS or Android.

4. Installing and Activating DUO Mobile
Duo Mobile is an app that runs on your tablet and helps you authenticate quickly and easily.
- Search for Duo Mobile in your app store.
- Download the app.
- Select "OK" when asked if Duo Mobile can send push notifications.
- Select Add Account
- Once the app is installed, click I have Duo Mobile installed.

5. Activate Duo Mobile
- If you are accessing an application protected by the Duo Universal Prompt, it will walk you through the enrollment process after you authenticate with your username and password:
- Next, you will be presented with a list of enrollment options.
We highly recommend using the Duo Mobile smartphone app, as it offers the best combination of security and convenience:

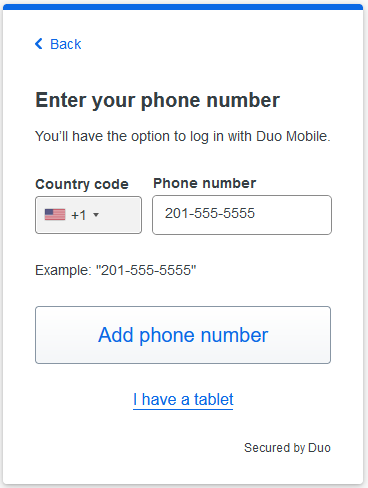
- If you choose the Duo Mobile option, you will be asked to enter your phone number on the next screen. If you have a tablet you can select that option:
- A text message will be sent to your phone number to verify ownership:

- After ownership of the phone is verified, you will be instructed to download the Duo Mobile app, available for iOS and Android:

- Once Duo Mobile is installed on your phone, open it. Make sure to enable notifications for the app.
Click on Next in the prompt on your computer, and either scan the QR code provided, or choose to have an activation code emailed to you:

- Your enrollment is complete! You have the option of adding a backup authentication method. If you choose to skip for now, you can click the "Log in with Duo" button to proceed with the login process:
The Duo Universal Prompt supports the use of a WebAuthn/FIDO2 Security Key for authentication. Please make sure your security key and browser meet the requirements listed here. The dialog boxes you see outside of the Duo Universal Prompt can vary between browsers and operating systems.
NOTE: The NetID Center and AITS Duo Prompts do not support WebAuthn. Because of this, you will want to add another authentication method such as the Duo Mobile app as a backup.
- Once the Security Key option is selected, click Continue. You may see a dialog box from your browser next. If the security key is already recognized by your browser, you can skip to step 2. Otherwise, select the option for 'External security key or built-in sensor':

- You will then see a dialog box from your operating system. Once you proceed you will be asked to set your security key PIN. If you have not set a PIN yet you can create one.

- Once your security key is verified and authorized you will be asked to touch your security key to complete the authentication.

- You're done! As previously mentioned, you will want to have an additional authentication method as a backup in case you encounter an application protected by the AITS Duo Prompt such as Banner or the NetID Center.
Support
If you have any issues with setting up or changing your Multi-Factor Authentication, please contact the ITS Help Desk by emailing techsupport@uis.edu, calling (217)206-6000, or stopping in the Lower Level Lounge of Brookens Library.
FAQ
Why did the university eliminate SMS passcodes as an option in Duo for Multi-factor Authentication?
While SMS-based authentication was once common, it is now considered less secure* due to vulnerabilities like SIM swapping and phishing.
Using other factors such as a key or app offers a more robust and industry-standard approach to securing access, aligning with best practices used by financial institutions, government agencies and peer universities. The university handles sensitive data that requires strong protection like personal information, academic records and research information.
*The National Institute of Standards and Technology (NIST) has deprecated SMS as a secure MFA method since their 2017 revision of Special Publication 800-63.
Is the university’s data really sensitive enough to justify this change?
Yes. University systems contain confidential student, faculty and research data. Protecting this information is a legal and ethical responsibility, and stronger authentication methods help prevent breaches and identity theft.
Why not require Multi-factor Authentication only for accounts with sensitive data?
Security is most effective when applied consistently. Selective enforcement creates gaps that attackers can exploit. A unified approach ensures that all users benefit from stronger protection and simplifies support and policy enforcement.
What if I don’t have access to a smartphone?
We understand that not everyone has access to the same technology. The university offers alternative authentication options such as hardware tokens. Please contact the Help Desk to explore these options.
Why is there a limit on Multi-factor Authentication bypass codes?
Limits on bypass codes help prevent abuse and maintain system integrity. Unlimited bypass codes can undermine security benefits. Bypass codes are one-time solutions available from the Help Desk to use as a last resort if no other method of MFA is available. If you’re experiencing issues, the Help Desk can assist with temporary access and explore long-term solutions.